SAML2 Authentication With ODOO13

Hey everyone, today I am gonna be talking about implementing SAML in odoo13. This is the problem I faced a while ago. Although a plug-in is already present for the Odoo version 12 designed and developed by the Odoo OCA community, that plugin is specifically designed for the Odoo v12. We will try to make that plug-in work for Odoo version 13. We’ll break the problem in the following parts and would explain and progress accordingly. We will be using OAuth with SAML as a means of third party authentication with Odoo.
NOTE: We’ll be using the Odoo.sh saas platform for Odoo13
a. What is SAML
b. Studying the plug-in and modifying it
c. Using OAuth
d. Setting up Odoo13
a. What is SAML
SAML stands for Security Assertion Markup Language. The main purpose of SAML is to enable Single Sign-On(SSO) feature. SAML eliminated the need for storing user credentials in multiple locations, it also eliminated the need for the user to authenticate multiple times for using the services offered by the SP. So before diving deep into the SAML, I’ll familiarize you with two terms that we would be using throughout the blog. The terms are IDP and SP.
The IDP stands for IDentity Provider. The IDP if boiled down for understanding to the very basic level is nothing but a middleware that authenticates the users for the SP(Service Provider). The IDP contains user credentials, the access rights for the users among all the other things that are required to authenticate and build a user session. In our case, we’ll be using the Auth0 as an IDP.
The SP stands for Service Provider, in our case the Odoo. The SP whenever gets a request from a user to access the data, sends a request to the IDP and the IDP then authenticates the user sending back a message to the SP regarding the authenticated user. If everything goes well then the user can access the services of the Service Provider.
The SAML uses the XML for sending and receiving data. Due to the use of XML, the sending and receiving of data are a bit heavy as compared to other SSO feature that is JWT(JSON Web Token). Now we have a basic understanding of what SAML is we can now proceed further.
b. Studying and Modifying the plugin
You can use the following link to download the plugin offered by the OCA community for integrating SAML with Odoo.
Once you have downloaded the plugin, it’s time you open it in the text editor of your choice. Once you’ve opened it, it’s time we fabricate it to make it installable on odoo13. So when I was modifying the plugin, the only thing I needed to do was to remove the @api.multi annotations from the methods in the models defined because Odoo dropped the use of this annotation when it moved from Odoo12 to Odoo13. So, the first thing you need to do is to remove it from every place you see.
Once you’ve removed the annotation from everywhere, you just need to do a small change to fix a view file. Go to the views folder in the plugin and select the file named auth_saml.xml. In the file go to line number 40(just below the form tag) and cut the div that is just below the form tag and paste it inside the sheet tag present just below the div we just cut. The code for div which we cut is given below.
<div class=”oe_button_box” name=”button_box”>
<button name=”toggle_active” type=”object” class=”oe_stat_button” icon=”fa-archive”>
<field name=”active” widget=”boolean_button”
options=’{“terminology”: “active”}’/>
</button>
</div>
Once this is done you are all set to deploy this module in your Odoo13. Since we are using the Odoo sh version we first need to push this module to the git branch linked to our project in the Odoo sh. if you have no idea how to deploy a module in Odoo sh, then you can use the below link to go to the documentation which will guide you on how to deploy a module in sh.
Before pushing the module in Odoo sh, we have one final thing to do and that is to provide this module with the mandatory dependency named lasso. In your own server, you can use the following command to install lasso. In windows, you can use the link https://repos.entrouvert.org/lasso.git/ to install lasso(there are chances that you could end up installing a wrong dependency using the pip that’s why I have given the link). The lasso works fine in the Linux environment but it does give some overhead while installing it in windows(I’ll update the blog as soon as I get a breakthrough in installing the right dependency via pip).
apt-get install python3-lasso
Since we are using Odoo sh we can simply add this dependency in a requirement.txt file saving it in the same folder where the auth_saml folder is saved. Below is the screenshot of what requirement.txt file looks like for the auth_saml module.

As you can see in the above screenshot I’ve knowingly included the folder in which the requirement.txt file is present in order to give you guys an idea where the file is present.
After doing this, push all the changes to GitHub and wait while your project builds the branch in Odoo sh. Once the branch is built. Install the module and ta-da we are halfway through. If it didn’t get installed, please check if you followed the above steps properly.
Once the module gets successfully installed, you’d see a new menu item got added in the Setting>Users menu item. As shown in the screenshot below.

As you can see a new menu item named SAML Providers is added. That’s enough for now, we’ll go configure our IDP(Auth0) now before proceeding further.
c. Using OAuth
Go to the link given below and signup for Auth0, it’s free of cost and it’s simple and fast option for testing.
Once you’ve signed up, it’s time we create a new Application in the Auth0. The Auth0 is our IDP and the application would act as an endpoint which will be integrated with Odoo so that we can use the SAML feature provided by Auth0. In order to create an application, select the Applications option present in the left side menu as shown in the screenshot below.

As you can see I’ve already tested a bit, but you’ll go and create a new application, I’ll use the Odoo app throughout the blog to explain things further.
Once you’ve created a new application, you’d need to click on the application you created and go to the application and click on the Addons options and turn on the SAML web app option as shown in the screenshot below.

As soon as you turn on the option you’ll be presented with the following screen.
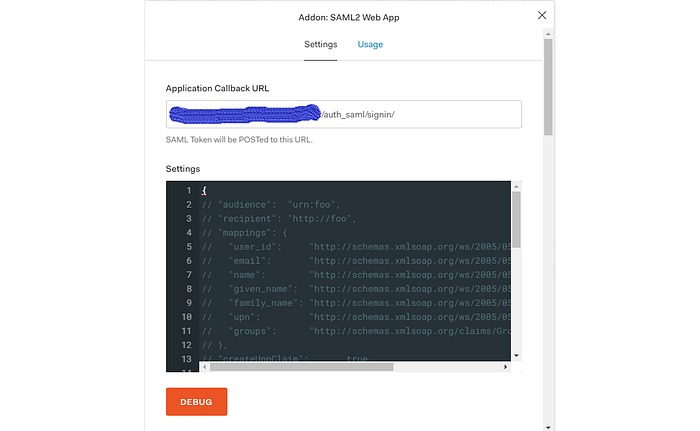
In the above screen, you can see an option for the Application Callback URL. In that textbox, you’d need to input your Odoo URL with a suffix of odoourl/auth_saml/signin/. This is important or else your authentication will be successful but you’d never be able to sign in to Odoo.
Once this is done, click on the Usage tab present in the pop up above. and in that tab find the option for Identity Provider Metadata: Download. Once you find the option download it(it’ll be needed later) and save the settings. From here the Auth0 part ends. Since our IDP is configured now, it’s time we configure the Service Provider(Odoo).
d. Setting up Odoo13
Now it’s time we configure our service provider. Open the menu item SAML Providers and create a new record.
i. In the Provider name section put in any name, I’ll just put SAML TEST
ii. In the Matching Attribute Section put in subject.nameId.
iii. In the IDP configuration section, please copy all the contents of the metadata file which we downloaded in the above step.
iv. In the SP Configuration section, copy and paste the below code and replace “odoourl” keyword with your actual URL.
<?xml version=”1.0"?>
<EntityDescriptor xmlns=”urn:oasis:names:tc:SAML:2.0:metadata”
xmlns:saml=”urn:oasis:names:tc:SAML:2.0:assertion”
xmlns:ds=”http://www.w3.org/2000/09/xmldsig#"
entityID=”odoourl/metadata">
<SPSSODescriptor
AuthnRequestsSigned=”true”
protocolSupportEnumeration=”urn:oasis:names:tc:SAML:2.0:protocol”>
<KeyDescriptor><ds:KeyInfo><ds:X509Data><ds:X509Certificate>Certificate</ds:X509Certificate></ds:X509Data></ds:KeyInfo></KeyDescriptor><AssertionConsumerService isDefault=”true” index=”0"
Binding=”urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST”
Location=”odoourl/auth_saml/signin" />
<NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</NameIDFormat>
</SPSSODescriptor>
<Organization>
<OrganizationName xml:lang=”en”>Example SAML 2.0 metadatas</OrganizationName>
</Organization>
</EntityDescriptor>
v. The last in the SP Private key section copy and paste the key from below(it’s the test key but in actual your URL’s SSL key will go in it).
— — -BEGIN PRIVATE KEY — — -
MIICeAIBADANBgkqhkiG9w0BAQEFAASCAmIwggJeAgEAAoGBAM5sy7T5U+siTqJm
LLS6Jul7LUw/BORUCnzz+1MU3ETF7icpxQUkpekkVT6VCmUPJmjcTsoHXmeSerwZ
NpmRJ75NuWU7F4yQ5zWX37MIvIPzWsWnb4fuZJBMeYYyCz0wOYzH+7Ev+wJtyneO
r5RCKL9zk3dlofEiCNVoGxSzqcv9AgMBAAECgYAr+6p76RQkaa7vk227JF7eKMzC
DjtwmyeQ8DuAvFUiojnYRmIgcmqXfpJbP05zsgKxHR/8lA1dbCySn5yuo+sfk0Js
biR6wESqx1dj6ippWqZz18dyH3ZWWSRJEapBk11cmy7Nq/+ox/ogM5/wOlGGNrJu
ieXRAl739Sj/cF/TgQJBAPGgQ6YoQ1bn/rhSUkdA90I1WMT7g1aKJSp35VYay2FN
z6EmzAXTt9QuOhvRdUXN+LuKap8PfLzHMwAxUazvfEkCQQDatHPsLrOLHLYHn/HG
3dKOrxiV+0eQlb9A52iUA3OJ3LTa8cWnc9XKLP40dcXrh5Jt9XKgga6LPhJhcURu
W8oVAkEAn1t6omBVoUCav0gT2cigCnuSkz/qLC4qOuseRv6e+grOkFM9Je6vg/IF
AwnO1X31uQKeNU+Kjhq2qT7dxjegeQJBAKNjhuse5LF8DJ3bpyQb2k8QjryV0pw4
034oo59YiLuo8FBVqYV1a3W0cWE9z1Qrn4CYiz9QQtbx04eKuEX+OxUCQQCzgGzi
Oi41nsy8uFr5s4joYfdZfDzezLz/GZNJ1q950Z69nJRVVTbQCvyJ2/Q+MtvojDXl
sIbngHtWnT36PTZS
— — -END PRIVATE KEY — — -
Once all is done just save the setting and open your Odoo URL in some other browser and see the SAML provider visible in the login form as shown in the screenshot below.

You can click on the link and you’ll be re-directed to Auth0 login. Once you log in successfully, you’ll be taken to Odoo. The best part is since the session is maintained at Auth0, you can logout and login without inputting credentials again until your session is active on the IDP side.
